A8Anon (Anonymizer as a Service)
A8Anon provides a rich palette of data protection techniques with fine-grained control. It has two core functions (1) Identify sensitive data (aka entities) (2) Apply the appropriate treatment to each type of entity. For example, you can configure that person names be pseudonymized and email addresses be redacted. You can also encrypt entites for subsequent decryption (2-way) or not (hashing). In automated mode, A8Anon will make these decisions for you.
Redaction
Pseudonymization
Encryption/Hashing
Generalization
Swapping
Perturbation
Secure User Functions
Case study: Legal contracts
Contract generation & review
Gen AI is a powerful technology for legal professionals. We’ve built a platform to generate, summarize, and redline legal documents. This uses a fine-tuned model trained on thousands of documents. These documents were anonymized to both improve tuning quality (for generalization) and preserve private data. A8Anon is deployed in the customers’ cloud. When used for summarization and redlining, A8Anon encrypts PII in all source documents and decrypts them within the legal firm’s private network. This provides the flexibility to use capable 3rd-party models instead of relying on limited in-house or open source LLMs.
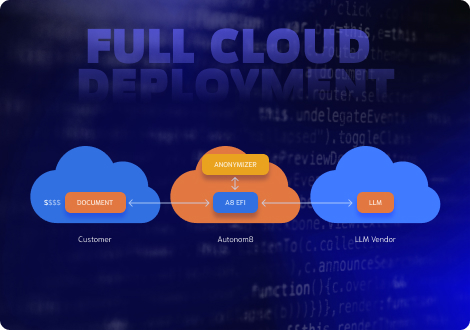
Deployment options for A8Anon
- A8Anon API
- Service hosted in the Autonom8 Google cloud (best price)
- Service hosted in your managed cloud (best data custody)
- Hosted on-prem (contact us for details)
What is Anonymization?
In our context, anonymization is the process by which textual data is cleansed of information (aka PII) which can identify a person, corporation, or transaction. The process first requires identification of PII in text, after which a variety of cleansing treatments can be applied to achieve the desired result. These techniques are briefly described below. A8Anon supports all these capabilities.

Redaction
Redaction is the process of masking PII in text. PII can be removed or obsured. For readability it is sometimes useful to perform partial masking e.g. leaving the last 4 digits of a phone number intact. A8Anon supports a variety of redaction styles including full and partial removal and obscuration with patterns such as LAST4 and ASTERISKS.

Pseudonymization
Pseudonymization replaces PII with false but plausible text. This maintains continuity of textual narrative but disguises identities. It is applicable to names, phone numbers, email and more. In retail situations consumers can be disassociated from their purchases or location. Pseudonymized prompts can be sent to LLMs without risk of identity disclosure. A8Anon enables a private key map for reverse lookup. Responses from LLMs can be mapped back to names which are meaningful to the consumer.

Encryption/Hashing
Encryption is the process of applying a cipher to change text to something which is implausible. Encryption is generally more applicable for numerical data e.g. quantity, price. By definition, encrypted data can be decrypted with a 2-way key. Encryption with a 1-way key is called hashing. Hashed text cannot be recovered. A8Anon supports encryption and hashing for all types of PII.

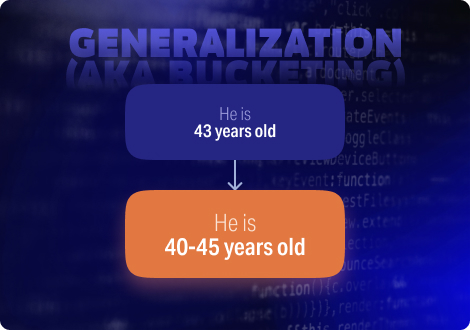
Generalization (aka Bucketing)
Generalization is an approach for grouping (mostly numerical) data into broader categories to hinder identifiability and thereby enhance privacy. These broader ranges are called buckets. Text such as “He is 43 years old” becomes “He is 40-45 years old”. Replacing a street address with a zip code is another example of generalization.
Additional techniques
- Perturbation: Adding noise to data to disguise numerical values such as salary or dates
- Swapping: Useful for values selected from a list. E.g. If customers are classified as ‘blue’, ‘silver’, and ‘gold’, we can shuffle these values
- Secure user actions: Let users run their own code when certain data classes are detected

Our Clients






















Media Mentions
Success Stories
Unlock intelligence in every step of your customer workflow.
Here’s how our customers did it with our robust Autonom8 platform.







 Read our reviews on G2 Crowd
Read our reviews on G2 Crowd





