


As per the Indian Government's privacy regulation for Aadhaar, of India (UIDAI’s authentication division) dated Jul 25th, 2017, encryption (masking) of Aadhaar Number and any connected data is mandatory before storing images of Aadhaar cards in databases. (circular 11020/205/2017)
The EU has introduced a new set of data rules known as the General Data Protection Regulation (GDPR) applicable from May 25th 2018 that will apply to any business that handles the data of EU nationals (including their staff), with very strict penalties for violation. The requirements include ensuring data usage only as intended and encryption of data with access controls
The EU has introduced a new set of data rules known as the General Data Protection Regulation (GDPR) applicable from May 25th 2018 that will apply to any business that handles the data of EU nationals (including their staff), with very strict penalties for violation. The requirements include ensuring data usage only as intended and encryption of data with access controls

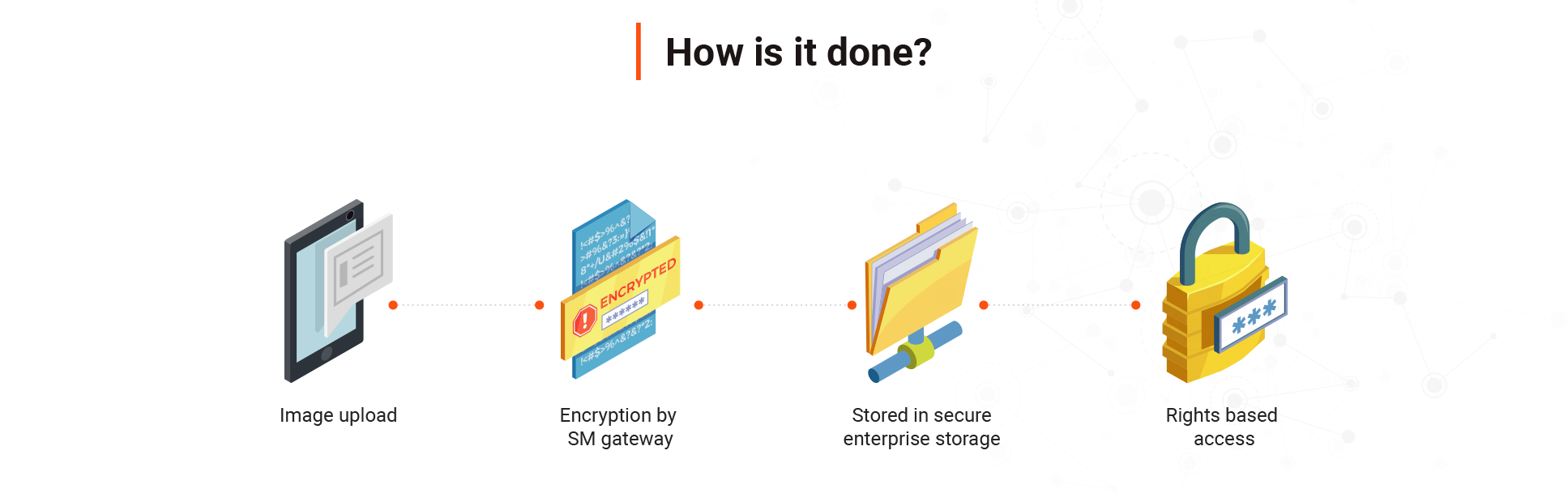
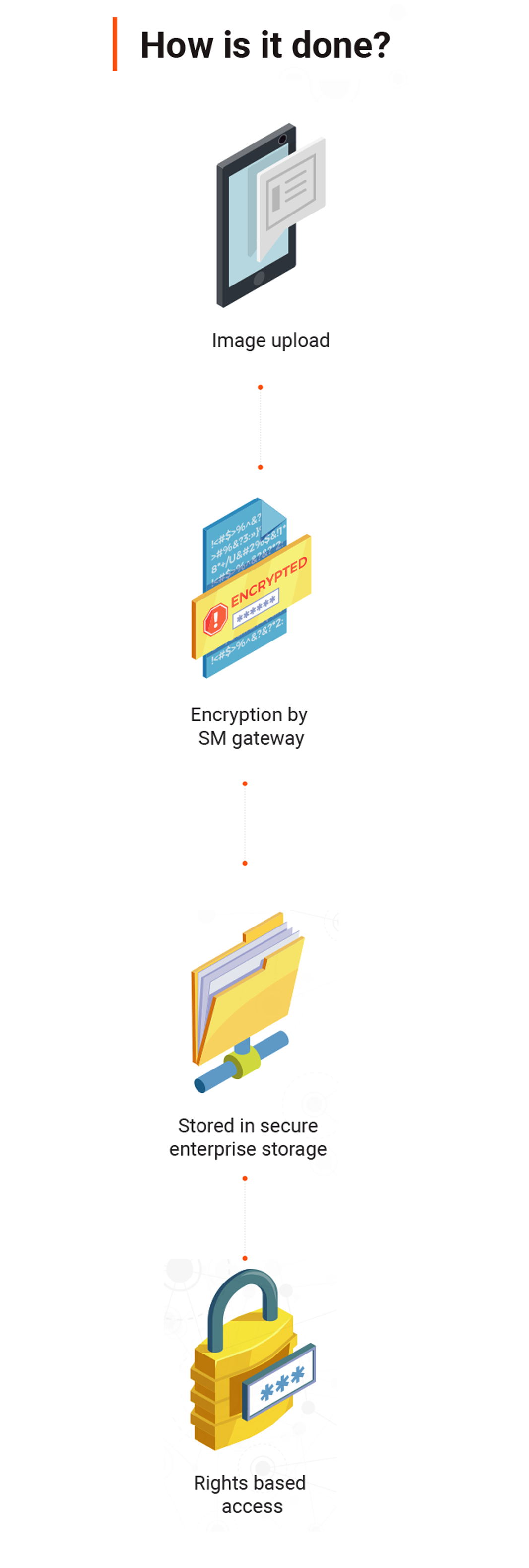


Typically clients have a data vault to house secure images. We recommend deploying a Secure Mask gateway that will provide access to the images based on user privileges. These user privileges would be defined by existing authentication and authorization systems.
Once we have an initial discussion with the customer around the existing infrastructure (data vault and authorization systems), we expect to deploy this solution within a week.
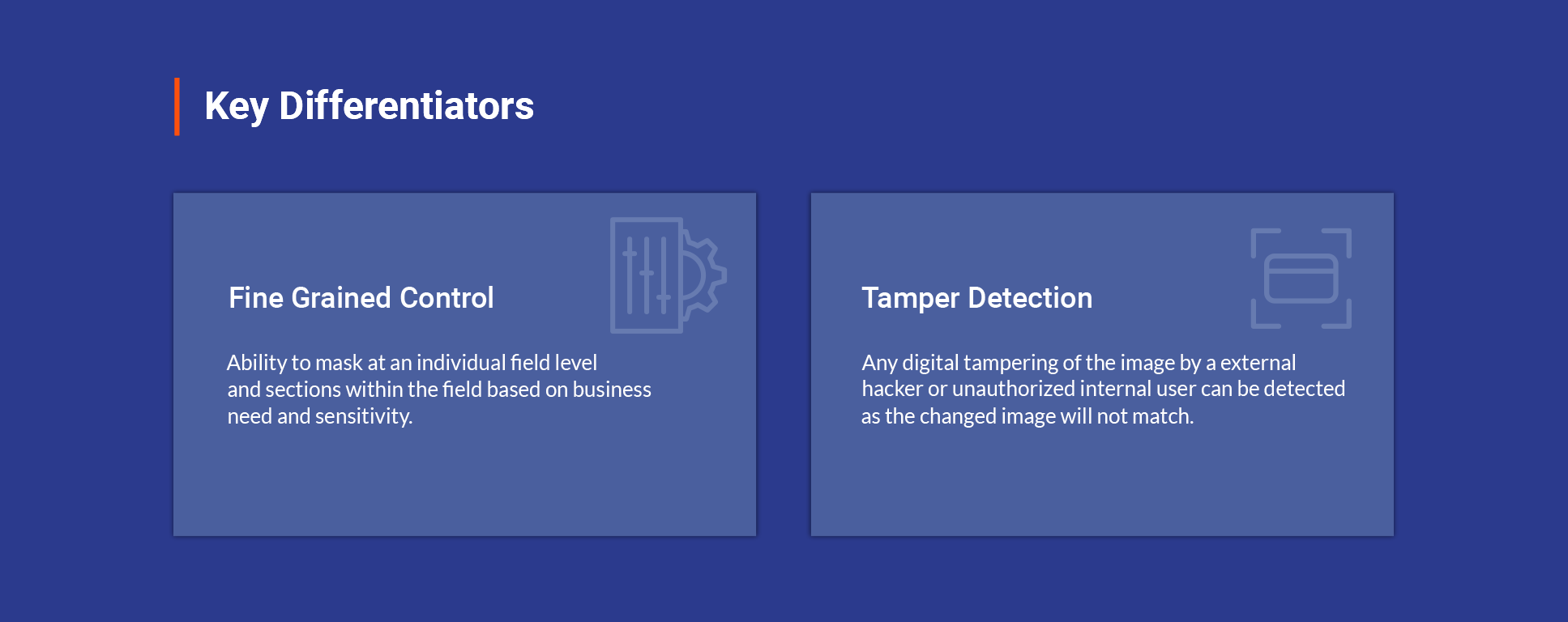
You could decide to control access for fields and details within a field, based on user groups with varying degrees of access. As an example, you might decide to show a small set of privileged users the complete account detail, another group of users only the last four digits while broader operations team see the field fully masked. You could also define alternate masking patterns like displaying alternate characters, first 3 characters etc.
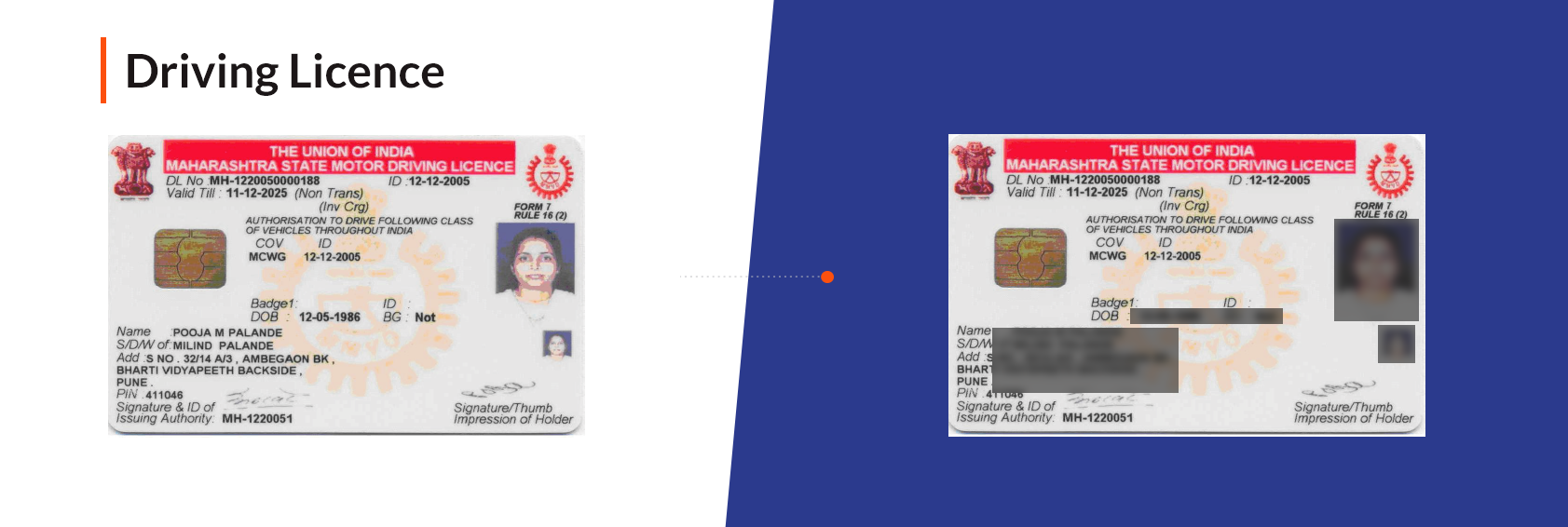
Given the contextual nature of masking, we need to configure the Secure Mask based on the document structure. We currently handle a range of sensitive documents around user identity and related to financial details. These include Driving License, Pay slips, PAN cards (India Tax identification), Aadhaar (India Unique Identity). We are constantly expanding the range of documents covered and can work to prioritize your documentary requirements
We use the Advanced Encryption Standard with 256 bit keys for encrypting information. AES is the first (and only) publicly accessible cipher approved by the United States-National Security Agency (NSA) for top secret information.
Typically clients have a data vault to house secure images. We recommend deploying a Secure Mask gateway that will provide access to the images based on user privileges. These user privileges would be defined by existing authentication and authorization systems.
Once we have an initial discussion with the customer around the existing infrastructure (data vault and authorization systems), we expect to deploy this solution within a week.
You could decide to control access for fields and details within a field, based on user groups with varying degrees of access. As an example, you might decide to show a small set of privileged users the complete account detail, another group of users only the last four digits while broader operations team see the field fully masked. You could also define alternate masking patterns like displaying alternate characters, first 3 characters etc.
Given the contextual nature of masking, we need to configure the Secure Mask based on the document structure. We currently handle a range of sensitive documents around user identity and related to financial details. These include Driving License, Pay slips, PAN cards (India Tax identification), Aadhaar (India Unique Identity). We are constantly expanding the range of documents covered and can work to prioritize your documentary requirements
We use the Advanced Encryption Standard with 256 bit keys for encrypting information. AES is the first (and only) publicly accessible cipher approved by the United States-National Security Agency (NSA) for top secret information.
